Download PDF
Download page Password Management Infosheet.
Password Management Infosheet
This document provides an overview of the LiveVox password management functionality. It also includes general guidelines for the client-level SFTP credentials.
General Guidelines
Below are the general guidelines for LiveVox Portal (LVP) and agent portal access:
Username and Password
The username and password are case-sensitive. Restrictions on the password are listed below.
- Password strength is selectable at three levels:
- Medium: User and agent passwords must be a minimum of eight characters in length containing at least one digit and one letter. The password should not match the previous four passwords for that user or agent credential.
- Strong: User and agent passwords must be a minimum of eight characters in length containing at least one digit, one letter, and one special character. The password should not match the previous four passwords for that user or agent credential.
Very Strong: User and agent passwords must be a minimum of twelve characters in length containing at least one digit, one letter, and one special character. The password should not match the previous four passwords for that user or agent credential.
- The following ASCII printable special characters are supported: (space) ! " # $ % & ' ( ) * + , - . / : ; < = > ? @ [ \ ] ^ _ ` { | } ~
- If you change your password strength policy, for example, if you update your policy so that all passwords must meet the Strong Password level rather than the Medium Password level, the policy applies to all newly created users and agents immediately. However, this policy will only apply to existing users and agents when the system indicates that they must reset their passwords.
Permitted LVP users can set the account password temporarily and force the users or agents to change the password on the first login or when the password is updated. If permitted LVP users change the password for their own user account, they are not prompted to change the password. This feature is configurable at the client level and applied to both users and agents.
User and agent passwords expire after a specified period. The timeframe is configurable at the client level, is set to 90 days by default, and is applied to both users and agents.
The system locks out users and agents after a number of failed login attempts. The allowed number of failed logins is configurable at the client level for users and agents. By default, both users and agents are allowed 5 failed logins. This is configurable at the client level.
Passwords are encrypted for all users, meaning that passwords are not stored in clear text anywhere in the system including the database. LiveVox uses AES-256 encryption.
SFTP Site Access
Users can upload campaign files or retrieve generated reports from their LiveVox SFTP site. LiveVox uses the SFTP protocol by default. If you require FTP instead, please contact the LiveVox Customer Care Team at customercare@livevox.com.
- If you are utilizing the LVP's integrated FTP Browser, a user's LVP credentials are used (password requirements described above).
- If you are utilizing a 3rd party SFTP browser application, specific SFTP credentials provided by LiveVox are used. These credentials adhere to the following standards:
- SFTP usernames and passwords are case-sensitive.
- SFTP passwords must be a minimum of eight characters in length and contain at least 1 digit.
- SFTP passwords do not expire.
- SFTP encrypts commands and data both, preventing passwords and sensitive information from being transmitted in the clear over a network.
Security Settings
Users in the Sysadmin role can manage LVP users' and agents' password security settings through the Security tab of the Client editor.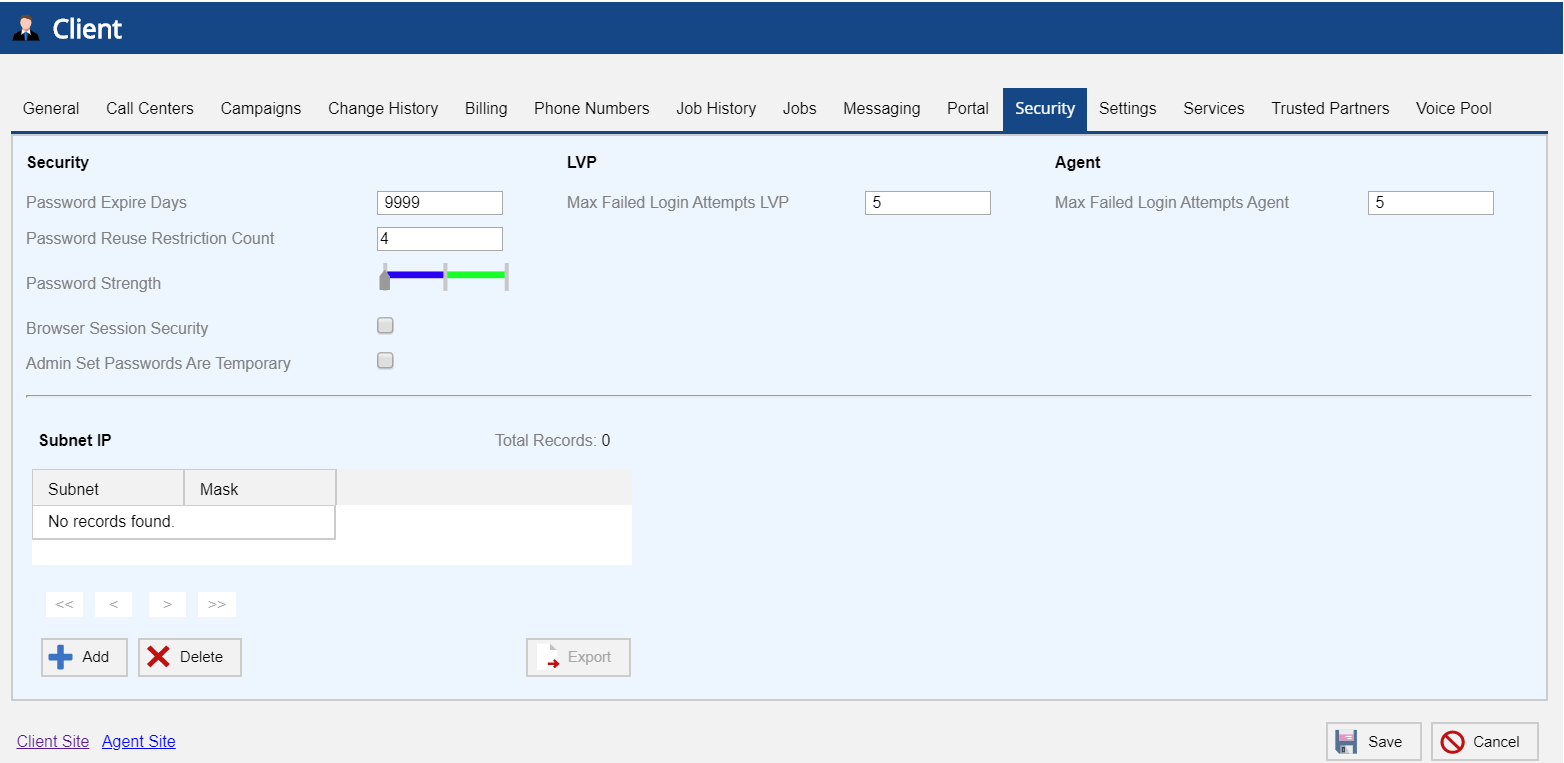
Sysadmins have the option to configure the following options for LVP users and agents:
Password Expire Days: Allows you to set the number of days for password expiration. Applies to both users and agents.
When implementing a password expiration period for the first time or reducing the number of days in the current period, it is recommended that all agents be logged out to prevent any call interruption due to password expiration. In addition, if your portal uses any LiveVox Custom Applications (Scripter, for example) or you are unsure if you have integrated these types of applications, contact your Account team before adding, removing, or making changes to the password expiration period as this might interrupt any active LiveVox Custom Applications.
- Max Failed Login Attempts: Allows you to set the number of password attempts after which the user or agent gets locked out. The value of Max Failed Login Attempts LVP and Max Failed Login Attempts Agent must be between 1 and 9. Zero, null, and characters are invalid.
- Password Reuse Restriction Count: Set the number of previous passwords that the user or agent cannot reuse when resetting the password. The minimum and the default value for this field is 4 and the maximum value is 25.
- Browser Session Security: If enabled, users must log back in any time the browser is closed.
Password Strength: Slide the arrow on the bar to select one of the following levels:
Medium: Passwords must be a minimum of eight characters in length containing at least one digit and one letter. Passwords must not match the previous four passwords.
Strong: Passwords must be a minimum of eight characters in length containing at least one digit, one letter, and one special character. Passwords must not match the previous four passwords.
Very Strong: Passwords must be a minimum of 12 characters in length containing at least one digit, one letter, and one special character. The password should not match the previous four passwords.
Admin Set Passwords Are Temporary: If enabled, the system forces the users or agents to change the password on the first login or when the password is updated. Once they log in with the temporary password, they are asked to change the password.
Setting up Agents and Users
Adding a New Agent
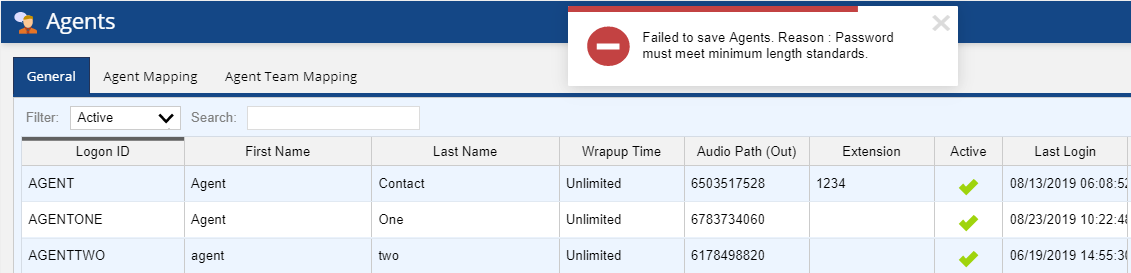
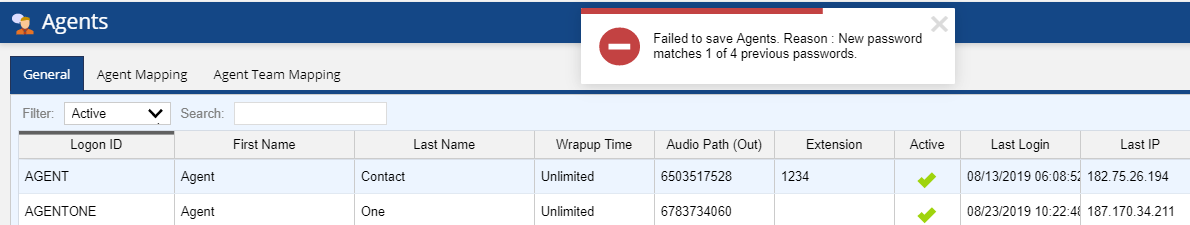
If the password does not contain the required or greater number of characters, does not contain a mixture of characters and numbers, or matches one of the previous four passwords, the user configuring the agent gets the following errors, after clicking the Save button.
- If the password has less than the required number of characters, the user configuring the agent gets the following error:
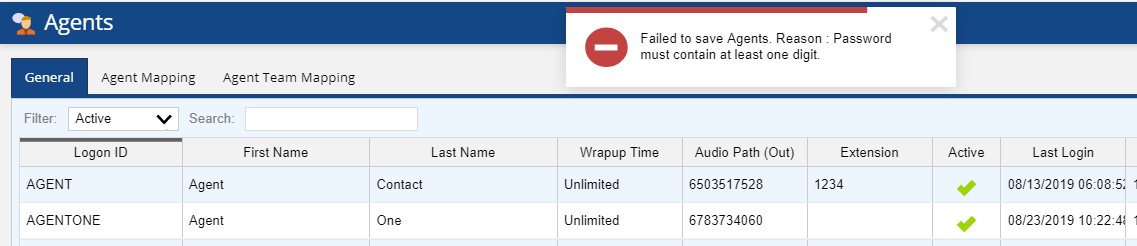
- If the password has no digits but characters only, the user configuring the agent gets the following error:
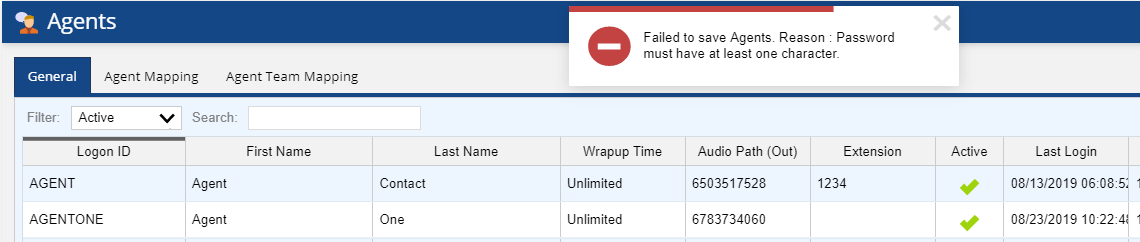
- If the password has no characters but digits only, the user configuring the agent gets the following error:
- If the new password matches with one of the previous four passwords, the user configuring the agent gets the following error:
Adding a New User
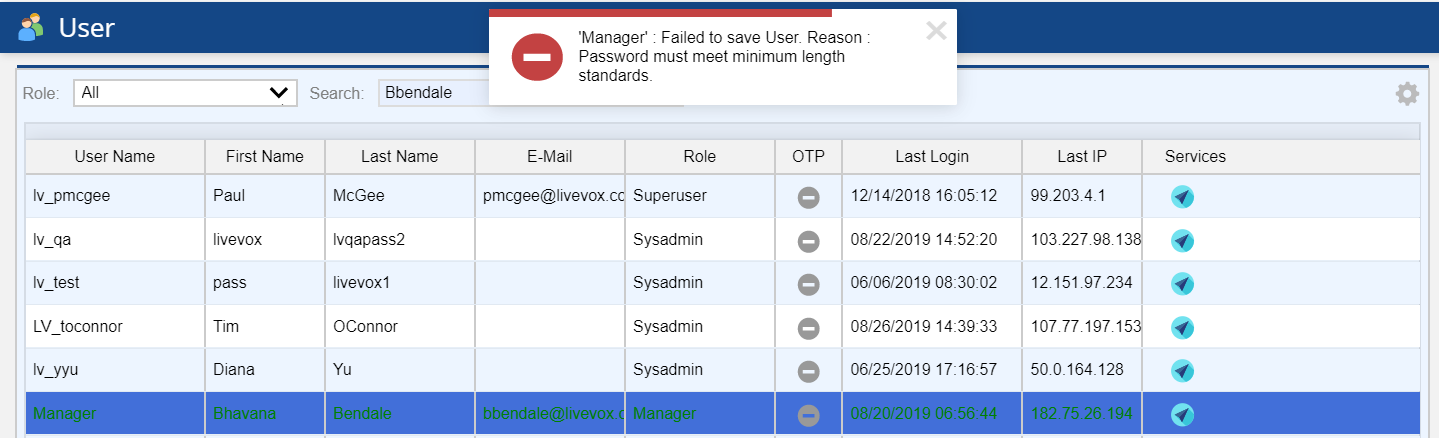
Similar to agent password errors, if the user password does not contain the required or greater number of characters, does not contain a mixture of characters and numbers, or matches one of the previous four passwords, the user configuring the agent gets an error, after clicking the Save button.
The below screen shows the example of the saving error as a password is not having the required number of characters. The user configuring the agent gets the following error:
Logging In
Agent Login
Agents can log in through the agent link provided by LiveVox. specify the Login ID and Password, and click Next to log in.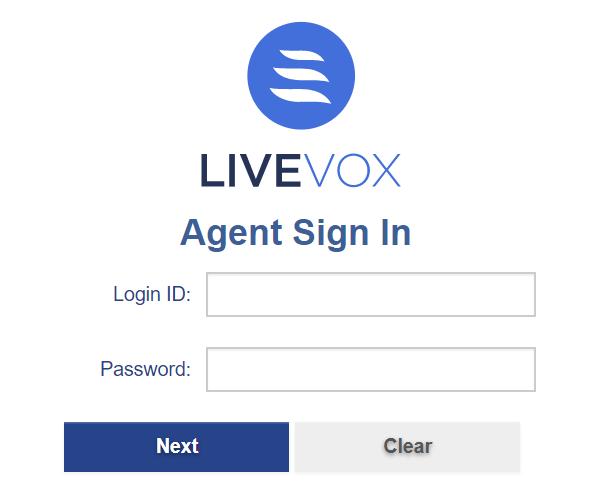
User Login
Users can log in through the user link provided by LiveVox. Enter the Client Code, User Name, and Password, and click Login to log in. 
If you are unable to log in, see the Failed Logins section.
If the account password is set temporarily, then the system forces the users or agents to change the password on the first login or when the password is updated. Once they log in with the temporary password, they are asked to change the password. For resetting the password, see the Resetting Expired Password section. If the Dual Factor Authentication (DFA) functionality is enabled, see the Changing Password with DFA section for more information.
Resetting Expired Password
When the password expires, agents and users get an error on their screen as they try to log in. A new password cannot be the same as the last four passwords.
Agent
The below screen shows the expired agent password error along with the Change Password pop-up. 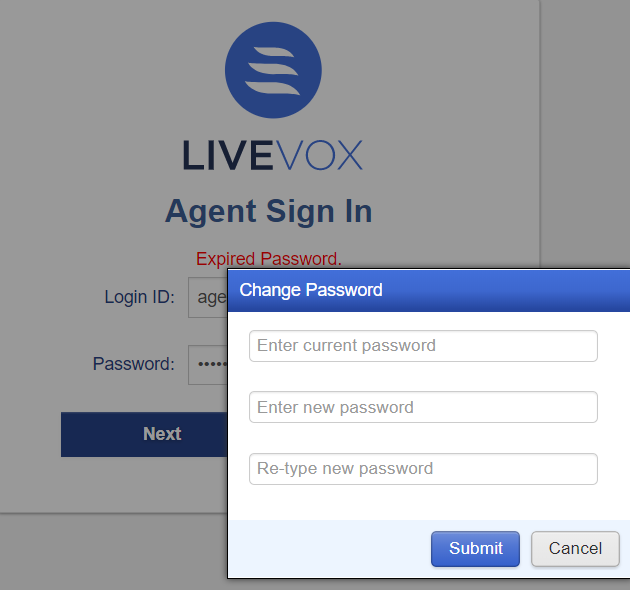
To reset the agent password, follow the procedure below:
- Enter the current password.
- Specify the new password.
- Re-type the new password.
- Click the Submit button to reset your password.
User
The below screen shows the expired user password message and options to set the new password.

To reset the user password, follow the procedure below:
- Enter the current password in the Old Password field.
- Specify the new password in the New Password field.
- Re-type the new password in the Retype Password field.
- Click the CHANGE button to reset your password.
Failed Logins
Agent
The below Agent Sign In screen displays the error message when an invalid password is entered by an agent.
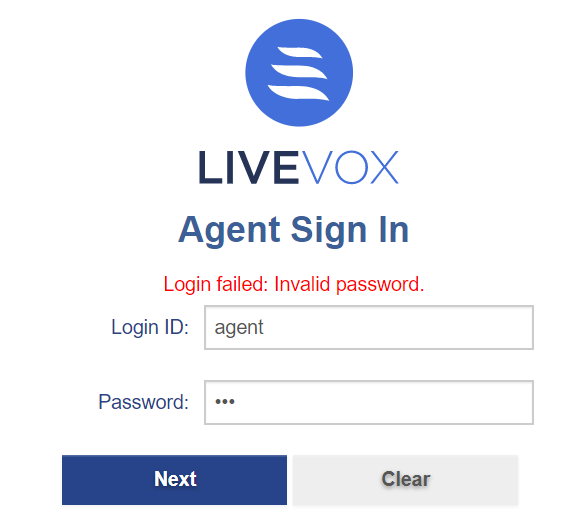
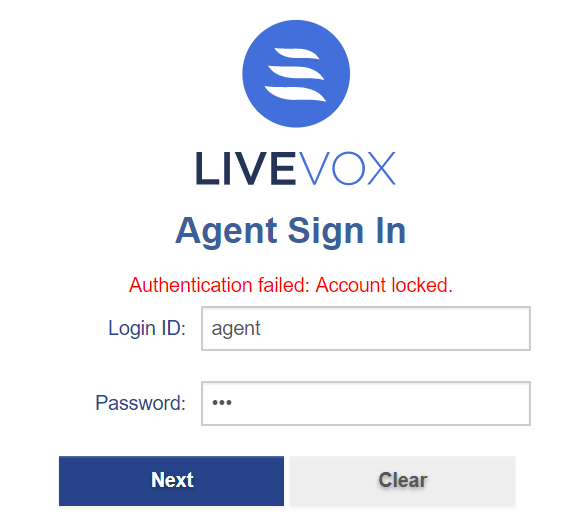
If an agent attempts to log in with the wrong password more times than the site’s configured limit, the agent is locked out and presented with the below screen:
User
The user login screen displays the message when an invalid password is entered by the user.

If a user attempts to log in with the wrong password more times than the site’s configured limit, the user will be locked out and presented with the below screen:

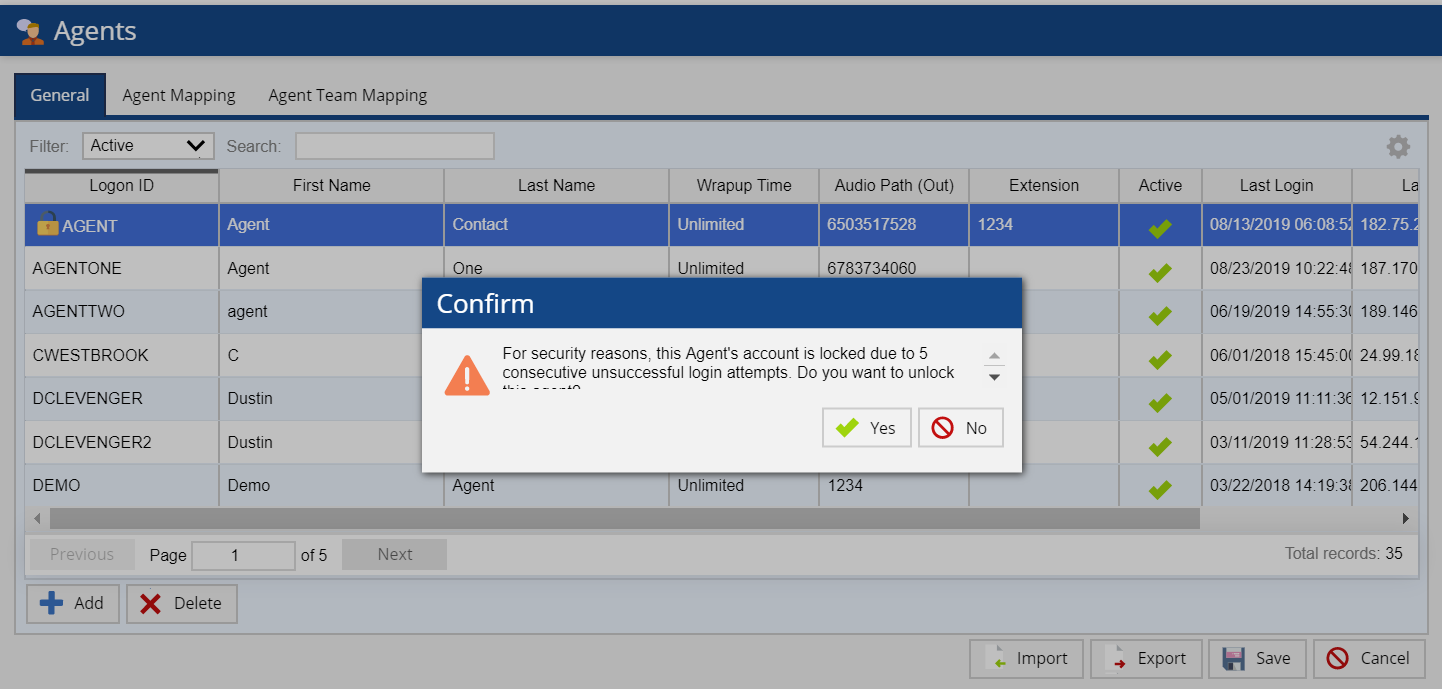
Unlocking User or Agent Account
To unlock the user or agent, a permitted user can double-click on the lock icon and confirm the action from the User or Agents editor.
Changing the Password
Users and agents can change their password after they log in.
Agent
Agents can change the password from the Agent Desktop. To change the password, follow the procedure below:
- Select the Change Password option from the upper-right drop-down menu in the Agent Desktop. The Change Password screen appears.

- Enter the current password.
- Specify the new password.
- Re-type the new password.
- Click the Submit button. The new password becomes effective immediately.
User
Users can change the password from the LVP. To change the password, follow the procedure below:
- Select the Edit User option from the profile picture drop-down menu in the upper right corner of the LVP. The User details screen appears.
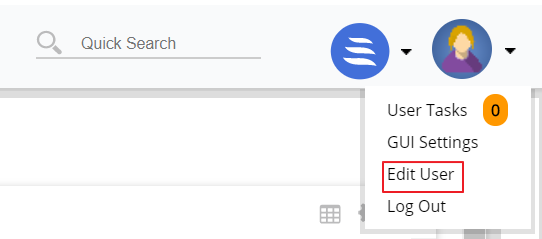
- Click the Change Password link on the User details screen. The Change Password screen appears.
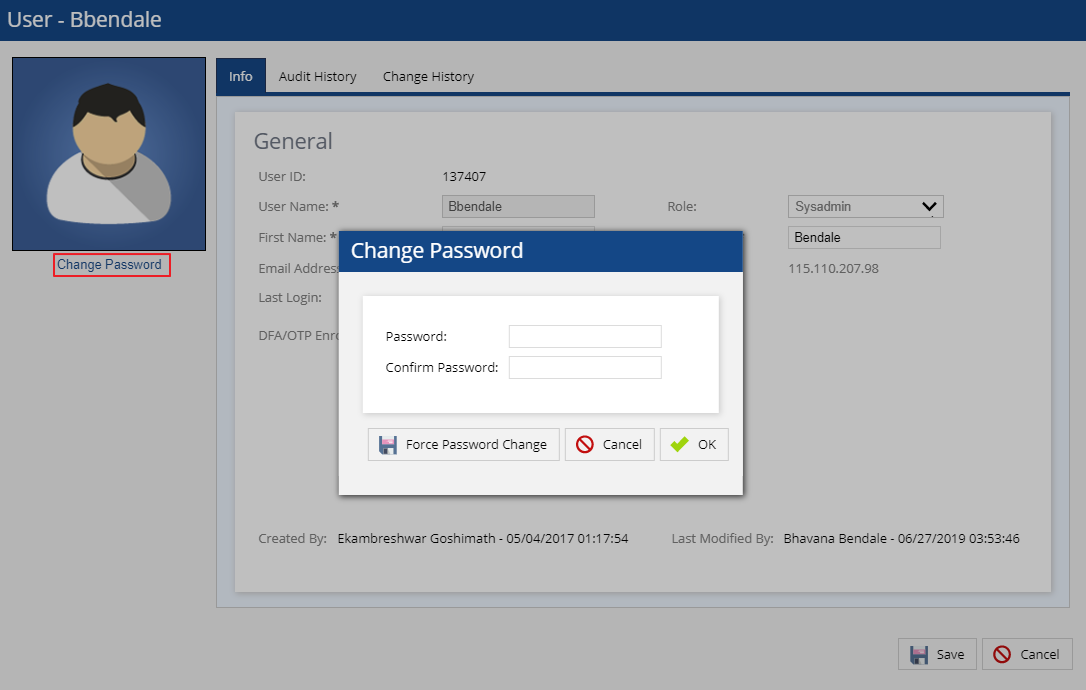
- Specify the new password in the Password and Confirm Password fields.
- Click the OK button.
- Click the Save button from the User details screen to complete your password update. The new password becomes effective immediately.
Dual Factor Authentication
Dual Factor Authentication (DFA) is a type of Multi-Factor Authentication where the second level of authentication is required for a successful login. The second password is an OTP (One Time Password).
- Contact LiveVox Client Services to enable the Dual Factor Authentication option and specify Max Failed Login OTP Attempts.
- Dual Factor Authentication is not available for agent login.
- Second-factor authorization is not supported through email, SMS, and voice message.
An administrator can enroll a user for dual-factor authentication. To enroll the user for DFA, navigate to Configure >System > Double click the user > General Tab. Click the Enroll button. A success message appears.
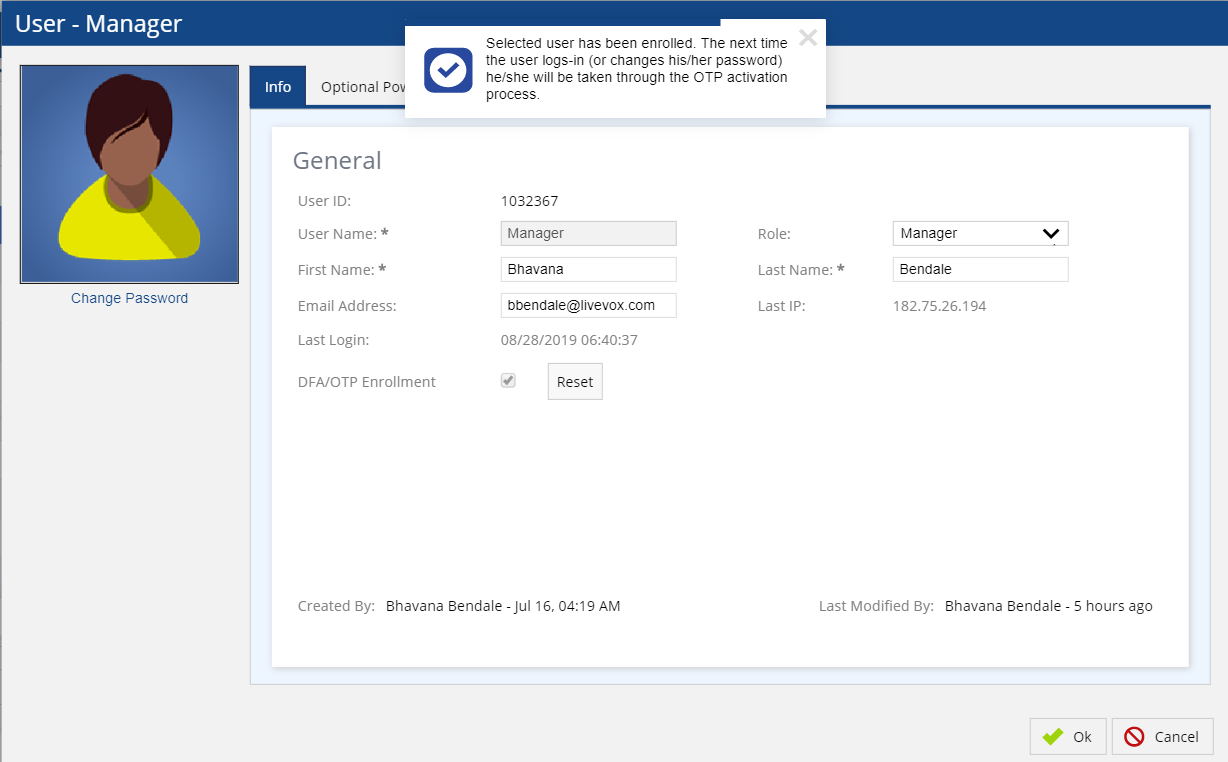
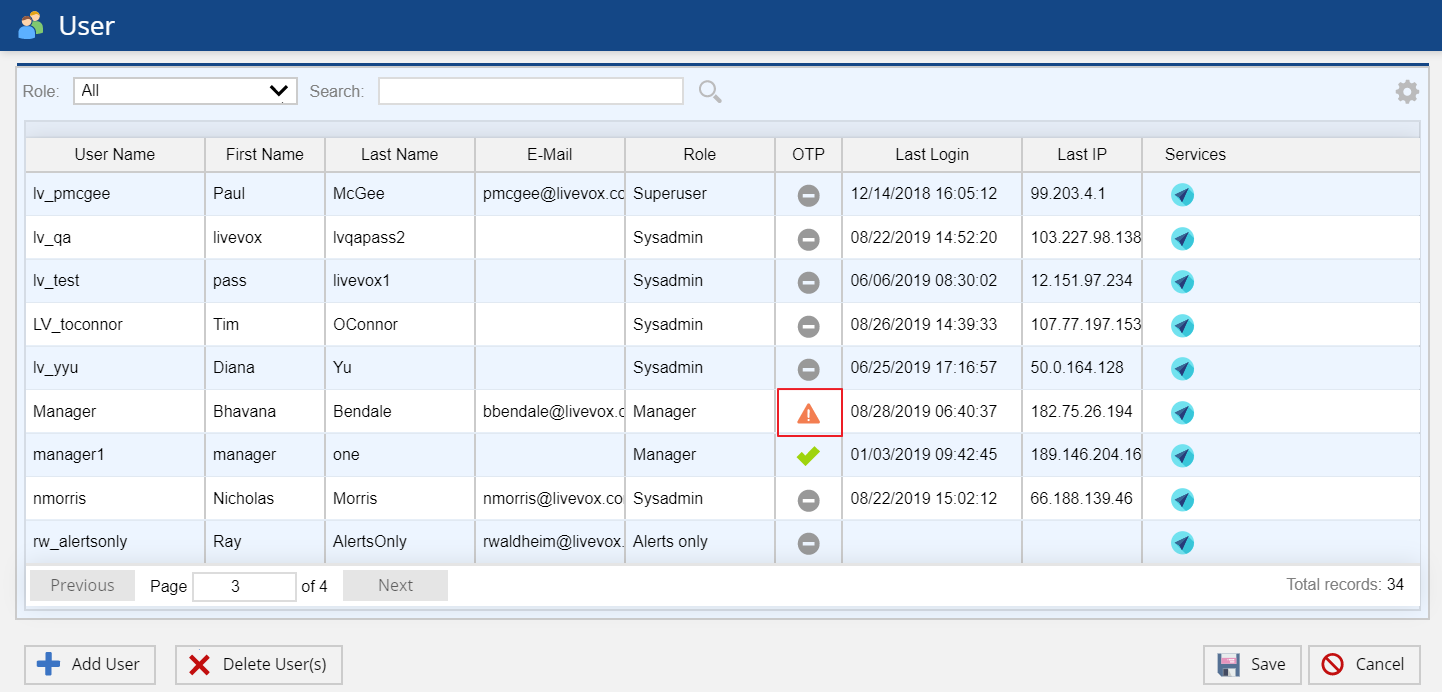
Once the enrollment option is enabled by the Administrator, the user’s enrollment is in pending activation status which is displayed in the OTP column of the User editor.
The user is required to complete this activation process upon login.
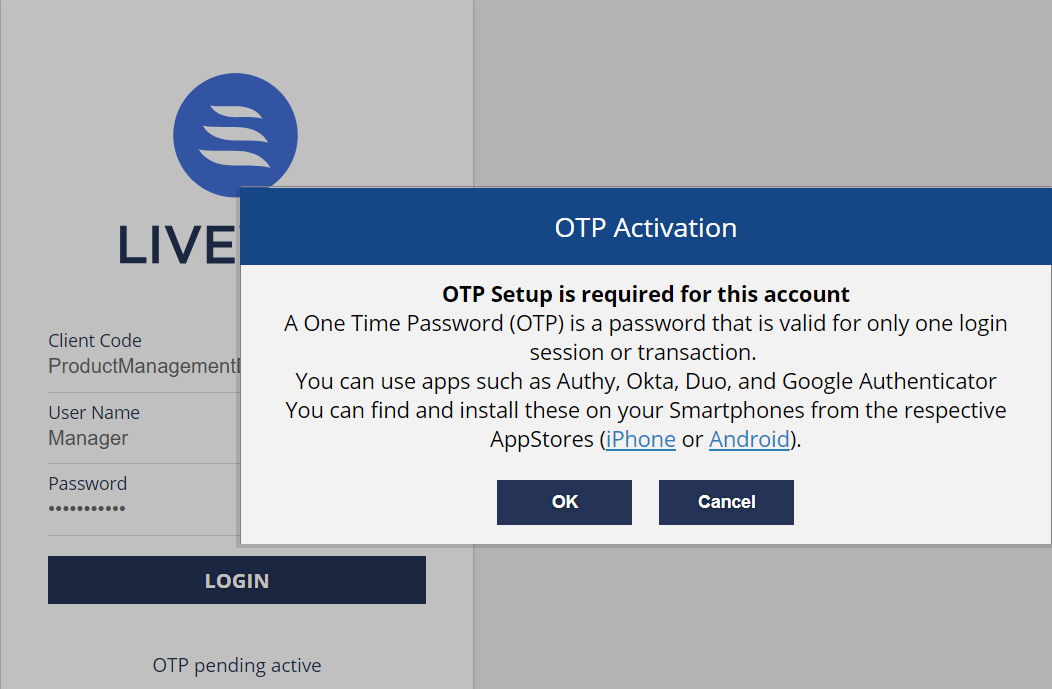
Users must authenticate their login with an OTP generated via Desktop Application (WinAuth), mobile application (Google Authenticator, OKTA, etc.), or hardware token.
User login (Users enrolled for DFA)
The below screen displays when the user is enrolled for DFA and submits the login credentials:
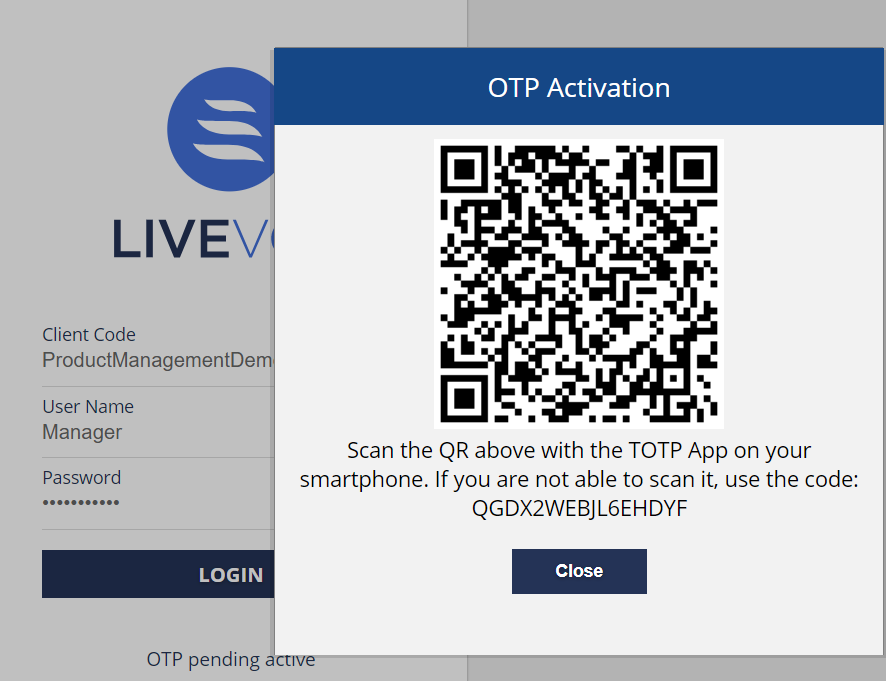
Desktop Users
Users are required to add the QR code in WinAuth to generate the OTP. Enter the OTP obtained through WinAuth application to continue the login process. For more information on the usage of WinAuth, see the Setting up WinAuth Application for Dual Factor Authentication section. 
Mobile Users
Users are required to scan the QR code to continue the login process. Then the user receives an OTP through a mobile application (Google Authenticator, OKTA, etc.). Enter the OTP obtained through the mobile application to log in.
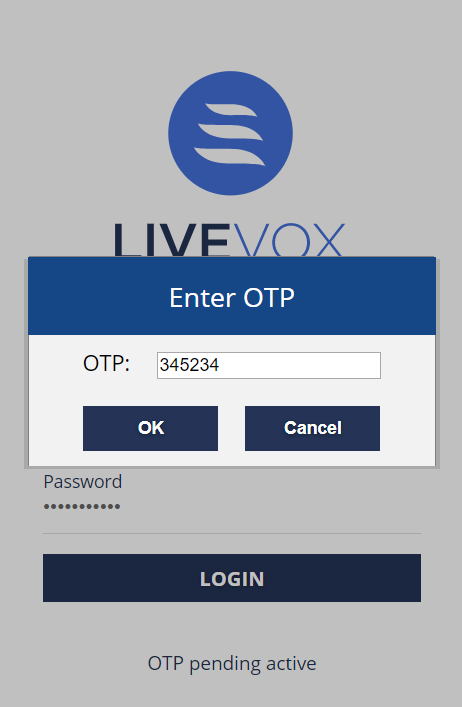
If there are failures, they are counted against the maximum OTP failure count, and eventually, the account gets locked. The user must contact the Administrator to unlock the account.
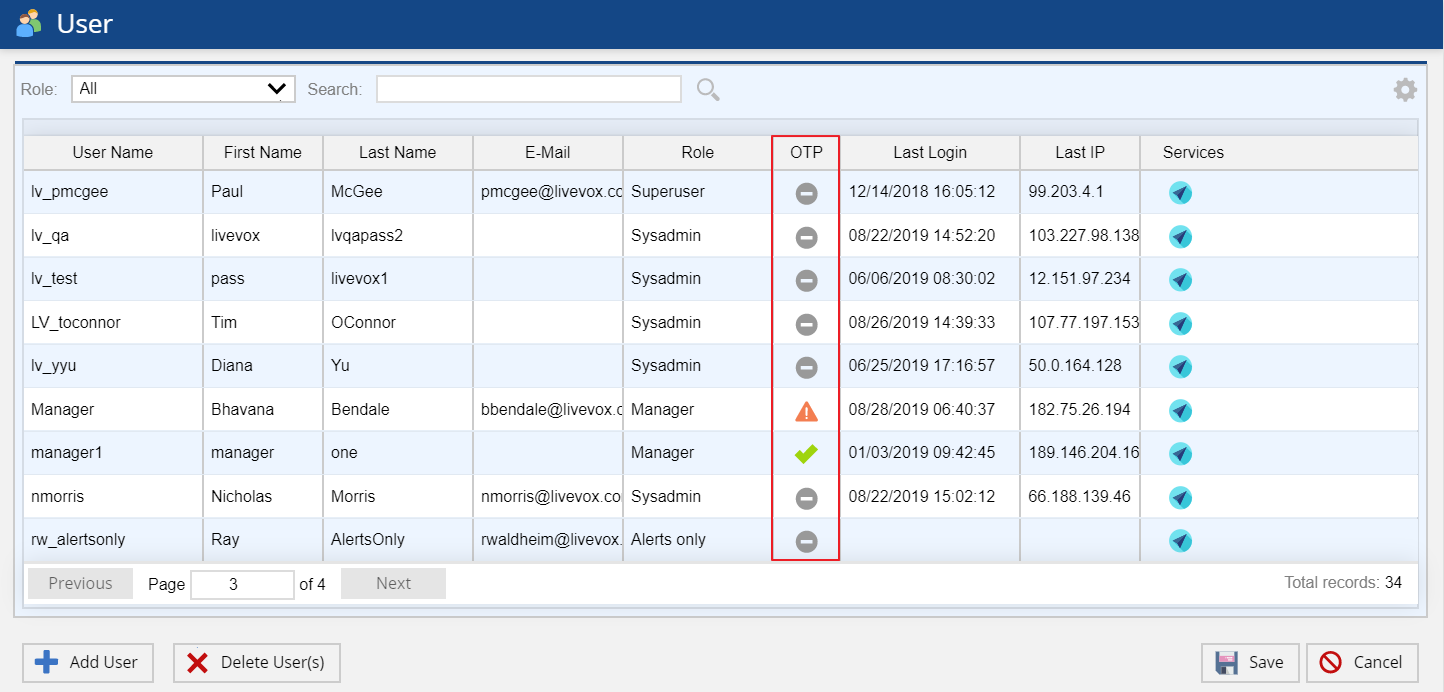
OTP Enrollment Status
The User editor's User Grid displays a column to indicate the OTP (One Time Password) Enrollment Status. Hover the mouse over the icon displayed in the OTP column to get the description of the OTP Enrollment Status.
Changing Password with DFA
The users enrolled for Dual Factor Authentication require a valid OTP token to change the password. The login process continues upon successful validation. The OTP token validation failure is counted against the maximum OTP failure count.
Resetting Locked Accounts
The User editor displays a lock icon for a user locked due to exceeding the maximum attempts of password or OTP. To unlock the user, permitted users can double-click the lock icon and confirm the action.
Setting up WinAuth Application for Dual Factor Authentication
The WinAuth application can be used by Desktop users to generate OTP for second-level verification. Follow the below steps for the initial setup of the WinAuth Authenticator.
- Download the WinAuth app by clicking https://winauth.github.io/winauth/.
- Once downloaded, double-click the WinAuth application to set up a new Authenticator:
- Click the Add button to set up an Authenticator. The Add Authenticator window appears.
- Specify the required information on the Add Authenticator window.
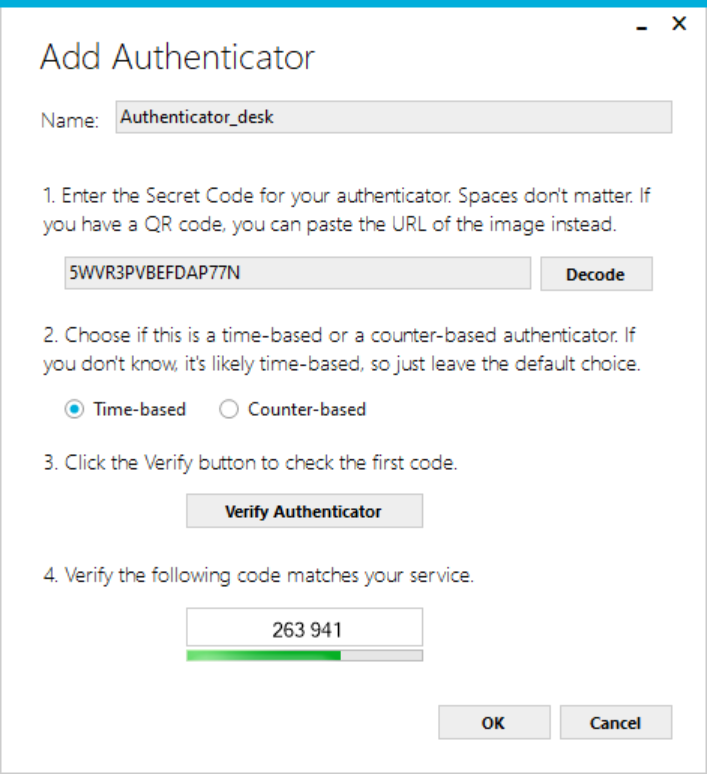
The Add Authenticator window allows you to configure the following fields:- Enter the name of the Authenticator in the Name field.
- Copy the QR code displayed on OTP Activation screen of LiveVox Portal into WinAuth application.
- Set the authenticator type as time-based.
- Click the Verify Authenticator button to preview the first generated code.
- Click OK. A Protection screen to lock the WinAuth application appears.
- If you want to lock the application, set a Password, and click OK. Use WinAuth to verify the OTP.
- Close the OTP Activation window of the LiveVox portal. You are prompted to enter OTP as shown in OTP verification through WinAuth screen, where you can enter the code presented on the WinAuth application.
LiveVox Customer Care Contacts
24 Hour Customer Care Line: (888) 477-3448
LiveVox Customer Care Email: customercare@livevox.com
This document is an unpublished work protected by the United States copyright laws and is proprietary to LiveVox, Inc. (“LiveVox”). Disclosure, copying, reproduction, merger, translation, modification, enhancement, or use by anyone other than authorized employees, clients or licensees of LiveVox, and its affiliate companies, without the prior written consent of LiveVox, is prohibited. This document is intended as a guide to assist users of systems provided by LiveVox, and does not constitute the provision by LiveVox of any legal or compliance advice. Compliance by authorized clients or licensees of LiveVox with any and all applicable local, state, federal, or foreign laws and regulations is the sole responsibility of those authorized clients or licensees. Further, features and services that rely on third Party performance are subject to the errors and omissions of those third Parties, over which LiveVox has no control. LiveVox therefore disclaims any and all liability resulting from or arising out of any services supplied by or through any third Party vendor or any acts or omissions of the applicable third Party vendor. Additionally, LiveVox makes no representations or warranties with respect to the accuracy of content supplied by Parties other than LiveVox.
For Internal and Client Use only